What happened?
On Wednesday, July 15, 2020, several high-profile Twitter accounts were hacked and used for a “smash-and-grab” type scam. The scam involved these compromised accounts sending out tweets requesting BTC donations to a wallet (presumably the hackers’), which would be doubled and returned to the donors.
The tweets generally followed this template – “I am giving back to the community! All Bitcoin sent to the address below will be sent back, doubled. Only doing this for 30 minutes.”
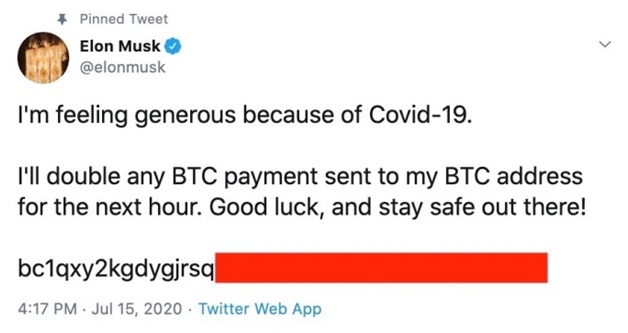
This is called a “smash-and-grab” because hackers have only a short time window to extract money from the scam before their operations are shut down.
The accounts hacked belonged to celebrities and public figures including – Joe Biden, Elon Musk, Barack Obama, Kanye West, Jeff Bezos, Bill Gates, etc. Several business accounts including those of Cash App, Uber, Apple, bitcoin, and coinbase. Other businesses accounts of cryptocurrencies were also compromised.
These tweets have since been taken down and control of the accounts in question have been returned to their owners.
The hackers have made out with an estimated $120,000, but this could turn out to be a conservative estimate as there are over 70,000 unverified transactions on the BTC wallet that was provided.
How did this happen?
Reports differ, but the consensus is that a group of hackers received access to an internal administrative tool used by Twitter employees, either by paying off employees, or other means.
This tool was apparently used to change account-level settings of the accounts, including confirmation mails, which were used to force password resets and gain control of even those accounts with multi-factor authentication.
The tool apparently consists of a panel that was used to change ownership of the high profile accounts that were hacked. Here’s a screenshot taken by a Twitter user of the panel.
The story is still developing and twitter has been mostly silent about this, but it has tacitly acknowledged that this was a “socially engineered” attack suggesting that employees might be involved.
It’s also come to light that the Twitter dev team was supposed to implement a new API on the day of the hack, this might be an alternative to the theory of social engineering, and the hack could be a case of someone exploiting bugs in the old API before the new one was implemented.
Who was responsible?
There is again no clear consensus.
Some of the tweets directed users to a website – cryptoforhealth.com, which also has an Instagram account on which the creators of the account took credit for the hack and stated that the money is for “charity”.

Other reports indict members of a hacking forum “OGUsers” who state that they had already been using the internal admin twitter tool for this scam and the scam on July 15 was simply an escalation.
Why was this done?
Theories abound that this was more than a scam and was politically motivated or motivated by business interests due to the nature of the accounts that were hacked.
It’s been speculated that this attack’s purpose is blackmail as the hackers could access the DMs of the hacked accounts. It could also be a demonstration to a client given the relatively small amount of money extracted.
How is Twitter reacting?
Jack Dorsey has stated that twitter is looking seriously into these attacks and that the usage of the internal tool in question has now been limited.
Most accounts should be able to Tweet again. As we continue working on a fix, this functionality may come and go. We’re working to get things back to normal as quickly as possible.
— Twitter Support (@TwitterSupport) July 16, 2020
Experts say that given the access that the hackers had, this could have been much worse.
What does this mean for you?
All of us use social media regularly for a host of activities. This high-profile attack should serve as an indication to both individuals and businesses, that we must take our cyber security more seriously.
Here are some precautions for both individuals and businesses, to safeguard themselves from spam-based attacks online.
How can individuals & businesses protect themselves against spam-based attacks?
Spam-based attacks rely on hackers getting a hold of email IDs, so here are precautions individuals can take to protect themselves from this attack.
- Do not post email addresses in public forums, chat rooms, or untrusted forms
- Only subscribe to trusted newsletters
- Use multiple & disposable email addresses
- Use a spam filter. These come in two types – content-based & source-based. Generally source-based filters are harder to get past
- Use long email addresses as these are less susceptible to brute-force attacks
- If you receive a spam email:
- Do not click on it
- Do not download any attachments from it
- Do not try to unsubscribe from the message
- Report it
- Generally be wary of suspicious-looking emails, forms, pop-ups or websites, and never post your email to any of these
Here’s how businesses can safeguard themselves from spam-based attacks:
- Make sure the SMTP server you’re using
- Does not relay unauthorized mails
- Has implemented client authentication
- Defines a maximum number of recipients per message
- Uses separate ports for submission and message relay
- Make sure your ISP
- Stops all open relays
- Controls open proxy servers
- Implements rate limits in outbound email traffic
- Monitors web-based email submission forms
- Logs sources of mails generated within the network
- Restrict network admin rights to a handful of people
- Invest in cybersecurity software and strong firewalls
- Encrypt and backup all your important data and store it offline
- Keep your hardware safe
- Educate employees on cyber security best practices
- If possible, follow the zero trust approach:
- Verify every user
- Validate every device
- Limit access based on user roles & requirements