Background Verification in the Digital Era
Establishing trust and authenticity has never been more crucial in an increasingly interconnected world where interactions span digital platforms and virtual landscapes. Background verification is a multifaceted endeavor, encompassing a spectrum of methodologies tailored to specific needs.

From criminal record checks and educational qualification validation to employment history verification, organizations can utilize diverse methods for background checks to ascertain the accuracy and authenticity of the information acquired from individuals. Each technique addresses distinct aspects of an individual’s background, contributing to a comprehensive assessment.
Cutting-edge technologies such as OCR, image recognition, facial matching, document categorization, and digital signatures can be integrated with AI-powered background verification software to streamline digital verification and onboarding processes, delivering unparalleled time and cost efficiency. Organizations can elevate background screening with a scalable and fortified approach, harnessing automation, seamless integration, and robust data security.
What is Background Verification?
Background verification, commonly referred to as background checks or screening, is the practice of investigating and validating a person’s private, professional, educational, and criminal history to evaluate whether they are qualified for employment, tenancy, loans, or other purposes. It entails gathering data from numerous sources to verify the veracity of the individual’s assertions and gauge their level of risk.
The Need for Background Verification: Building Trust and Security
In a landscape riddled with uncertainties and potential risks, the imperative of background verification cannot be overstated. Organizations and individuals recognize the need to validate information, verify identities, and ensure the credibility of those they engage with. Background verification is the cornerstone of building trust, transparency, and security in an environment where reliability is paramount.
Background verification helps organizations and individuals make informed decisions by minimizing the risks associated with hiring, lending, renting, or any other engagement. It ensures that individuals’ information is accurate and reliable, maintaining the integrity of various processes and transactions.
Background verification is crucial in preventing various types of fraud and risks in the verification process. By thoroughly vetting candidates’ information, organizations can mitigate the following fraudulent activities:
- False Credentials : Background checks help uncover individuals providing false or exaggerated educational qualifications, work experience, or skills to enhance their profiles.
- Criminal History : Organizations can identify individuals or entities with undisclosed criminal records or convictions that might risk business growth and security.
- Identity Theft : Verification processes ensure that individuals are who they claim to be, preventing instances of identity theft or impersonation during the verification process.
- Financial Dishonesty : Background checks reveal any individual’s financial history, highlighting past issues such as bankruptcy, debt, or fraudulent financial activities that could indicate a lack of financial integrity.
- Misrepresentation : Background checks help uncover instances of individuals providing misleading information about their skills, experience, or accomplishments with forged or fabricated documents.
Background verification is a robust defense mechanism against various forms of fraud, enabling organizations to make informed decisions and safeguard their reputation and overall business integrity.
Types of Background Verification Methods
Various checks and screenings are available for background verification to cater to different purposes and requirements. These options offer a comprehensive view of an individual’s history and background, enabling organizations to make mindful decisions.
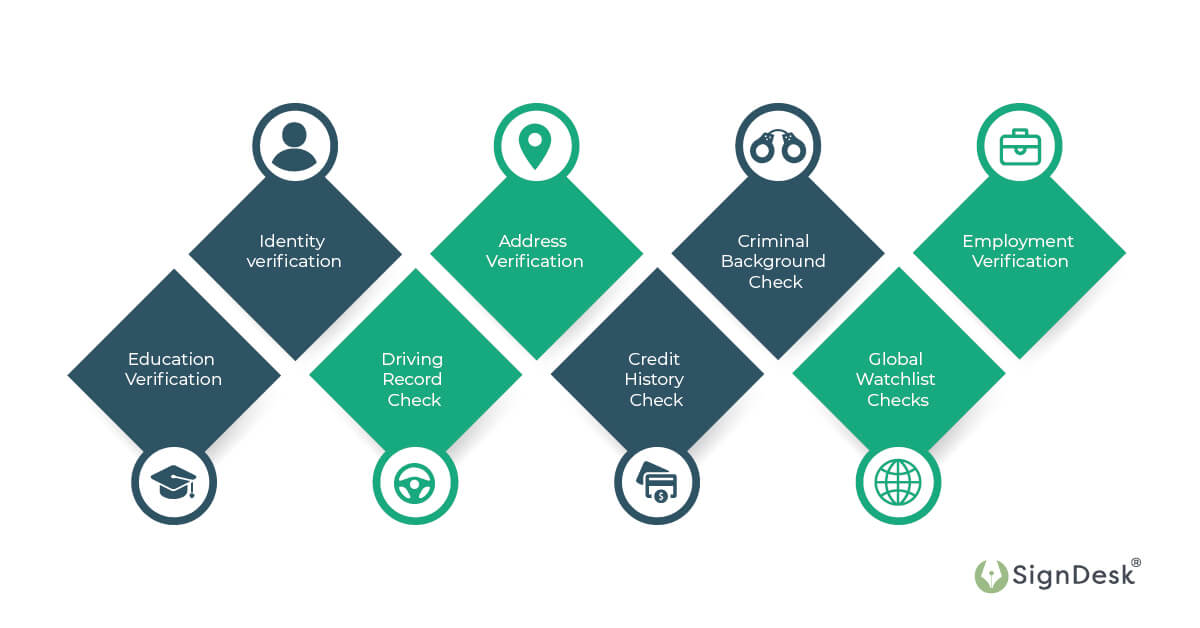
- Identity verification : With background verification, any individual’s identity can be verified instantly using their ID cards and other relevant data.
- Address Verification : Conducting an address check by cross-referencing it with official records and databases is a straightforward method to validate the candidate’s location and eligibility to work within a specific business jurisdiction. Verifying a candidate’s address details efficiently helps affirm their identity and is pivotal in confirming essential personal information.
- Criminal Background Check : This involves checking an individual’s criminal record to identify past arrests, convictions, or illegal activities. It helps assess the potential risk an individual might pose.
- Employment Verification : This process confirms an individual’s work history, positions, duration of employment, and job responsibilities. It ensures the accuracy of the employment details provided.
- Education Verification : An education check validates an individual’s educational qualifications, degrees, diplomas, and certificates. It helps verify the authenticity of academic achievements to determine a candidate’s eligibility.
- Driving Record Check : Assessing an individual’s driving history, including traffic violations, accidents, and license suspensions, is essential for roles that involve driving company vehicles.
- Credit History Check : Assessing an individual’s creditworthiness and financial history is particularly important in financial transactions and loan approvals. It provides insights into an individual’s financial responsibility.
- Global Watchlist Checks : Checking global databases for individuals involved in illegal activities, terrorism, or money laundering, ensuring compliance with regulatory standards.
Each type of background verification serves a specific purpose and can be tailored to suit the needs of different industries and scenarios. Organizations and individuals can choose the appropriate checks based on their requirements.
How To Navigate the Background Verification Process: BGV Steps
Background verification can be processed through various background checks using demographic data, biometric data, financial information, etc. Organizations can verify any individual by selecting their preferred background check step-by-step.
- Identity Verification and Address Verification – An individual’s identity and address can be verified using any ID card, e.g., PAN card, Aadhaar Card, Voter Card, Passport, Driving license, and Vehicle registration card. It extracts data and cross-verifies the individual’s details retrieved from the government database. ID verification APIs can instantly authenticate an individual.
- PAN Identification API – To authenticate identity, address, and other relevant data, check the step-by-step process for PAN-based KYC verification using APIs
-
-
- Log in to the Portal : The client accesses the portal through a provided link.
- Enter and Upload : The required customer details are entered, and an image of the PAN card is uploaded.
- Data Retrieval and Matching : The API retrieves validated data and compares it with the client-provided information.
- Verified : The verification process is complete if the details match.
-
The PAN number verification API streamlines background verification, enabling organizations to secure their onboarding process efficiently. With the PAN verification API, an individual’s credit history can be verified instantly. An adverse financial history check uncovers information about an individual’s unfavorable credit history, credit score, debt records, and instances of bankruptcy to assess their financial background, offering insights into their financial integrity and responsibility.
-
- Aadhaar Verification API – Aadhaar Verification API is another convenient way to retrieve any data about an individual, as the Aadhaar number is connected to all other documents and contains sensitive biometric information.
-
-
- Input : The client provides details such as name, address, date of birth, et cetera., for verification.
- Aadhaar Verification : The client inputs their Aadhaar number and receives an OTP on their registered mobile number.
- Generation of Aadhaar XML : The service provider generates a client-specific Aadhaar XML file.
- OTP Authentication : The client enters the OTP received on their mobile.
- XML Decryption : The Aadhaar OTP is employed to decrypt the XML file, retrieving information like name, gender, date of birth, address, zip code, and photo.
- Pre-Validated Verification : The obtained and pre-validated data is utilized to authenticate the client’s identification.
-
We offer the Aadhaar Masking API to mask personal information where the individual has no requirement to share the Aadhaar number.
-
- Passport Verification API – Passport verification API can verify background information about nationality and any sanctions against global lists in other countries.
-
-
- Upload: The user submits a digital passport copy through the verification portal.
- Data Extraction : The passport verification API employs OCR to extract personal details from the uploaded passport copy.
- Data Comparison :: The API cross-references the extracted data with validated sources.
- Verification Outcome : The client’s background verification is approved if the details align.
-
Once passport verification is successful, businesses can have the user authenticate contracts, sign agreements, and initiate their operations.
-
- Driving License Verification API – A driving license is a valuable background verification document confirming an individual’s identity, age, and legal driving status. It helps organizations verify authenticity, consistency, civil behavior, and potential issues related to driving.
-
-
- Initiation : The customer receives an invitation via email or SMS for KYC verification.
- Data Input : The customer provides their driving license (DL) number and date of birth or uploads images of their DL’s front and back.
- Image Capture : Live images of the customer and DL are taken.
- Automated Data Extraction : Optical character recognition (OCR) technology extracts data from the images. AI-driven verification algorithms then cross-reference this data with government databases.
- Data Validation : Extracted background verification details are compared with validated data through data aggregation.
- Verification Completion : DL verification is successfully concluded if the match percentage meets the required threshold.
-
- Academic Check – The academic achievement verification process, called an education check, involves authentication with the designated educational institution. This verification confirms details such as the attended institution, duration of attendance, subjects pursued, and achieved grades, or any professional certifications claimed by the individual.
-
- Digilocker API : With the Digilocker API, any document can be verified and cross-checked with data pre-validated in the Digilocker repository, as Digilocker is integrated with 1679 issuer organizations.
-
-
- Initiate Verification Request : The organization initiates the process by requesting document verification via Digilocker API documentation.
- Receive Digilocker API SDK : SignDesk’s integrated DigiLocker API SDK and API credentials are emailed to the organization.
- Input User Data : Users log in to the verification portal using their registered mobile numbers. Once consent is granted, the API can access their documents.
- Retrieve and Compare : The user’s specific document verification request is swiftly processed by retrieving and comparing the stored document from the Digilocker database.
- Document Validation : Organizations can verify an individual’s identity using any valid ID document. The verification status confirms legitimacy. In case of successful verification, the output data includes the individual’s name, gender, date of birth, and address
-
- Criminal Background Verification – With the court case APIs, organizations can perform background screening for any individual to assess their civil and criminal backgrounds and suitability for various roles, memberships, contracts, or other engagements that require a clean criminal record.
- Court Case API – Criminal Background Verification through Court Case APIs involves a systematic and technologically advanced process to ascertain an individual’s criminal history by accessing court records and case information using integrated APIs. This approach offers a streamlined and efficient way to gather accurate and up-to-date data on an individual’s criminal cases.
-
-
- Verification Request : The process begins when an organization or entity initiates a request for criminal background verification of an individual using the Court Case API.
- Integration of Court Case API : The organization receives access to the Court Case API and the necessary credentials. These credentials enable secure and authorized access to the court’s database, where the relevant case information is stored.
- Data Input and Consent : The individual undergoing the verification process must provide specific personal details, such as name, date of birth, and any additional identifiers like an Aadhaar or PAN number. The individual’s consent is also obtained to access their criminal records through the API.
- Query Execution : Once the individual’s data and consent are obtained, the API executes a query on the court’s database—the query searches for relevant case information associated with the provided details.
- Retrieval of Case Information : The Court Case API retrieves case information from the court’s database based on the individual’s provided details. This may include details of crime lists, criminal charges, court proceedings, number of cases, case category, case type, case details, risk profiles, and risk summary.
- Matching and Verification : The retrieved case information is compared and matched with the provided individual’s details. This step is crucial to ensure the accuracy and relevance of the retrieved data.
- Verification Result : The outcome of the criminal background verification is determined based on the matching results. If there are no matches found, the verification result is considered negative. On the other hand, if matches are found, the result is considered positive, indicating a potential criminal history.
-
The Business Impact of Comprehensive Background Verification
The advantages of conducting rigorous background verification ripple across various domains. Beyond the apparent risk reduction, a well-executed verification process cultivates an environment of transparency, accountability, and security. Organizations, institutions, and even individuals can benefit from the heightened level of confidence that stems from knowing that interactions are based on reliable and verified information.
Background verification software offers numerous benefits that enhance the efficiency, accuracy, and reliability of the employee screening and onboarding process.
- Efficiency & Scalability :Automated background verification software streamlines the entire process remotely, reducing manual effort, administrative burdens, paper-based documentation, and lengthy review cycles. The BGV process results in quicker turnaround times (TAT) with scalability for screening and hiring decisions, leading to cost savings over time.
- Accuracy : Background verification software tools eliminate the possibility of human errors associated with manual data entry and processing, ensuring accurate and reliable results for each candidate.
- Comprehensive Screening : Background verification software can perform a wide range of checks, including criminal history, employment history, education verification, reference checks, and more, providing a comprehensive view of the candidate’s background.
- Data Security : Top-notch background verification software employs robust security measures to protect sensitive candidate information, ensuring compliance with data privacy regulations and preventing unauthorized access.
- Integration & Customization :Background verification software solutions seamlessly integrate with existing HR systems and applicant tracking systems (ATS), enabling smooth data sharing and reducing the need for duplicate data entry. Organizations can customize the verification process to match their specific needs and industry requirements, tailoring the checks based on the nature of the job role.
- Audit Trail & Real-time Updates :Automated smart digital platforms provide real-time updates on the status of background checks and maintain a digital trail of the verification process, allowing HR teams and recruiters to stay informed about the progress with transparency and regulatory compliance.
- Risk Mitigation : By uncovering potential red flags, discrepancies, and risk profiles in background screening, the software helps organizations avoid hiring individuals with problematic histories that could pose risks.
Elevate Trust with Integrated Background Verification Software
Background verification is a procedural formality and a pivotal instrument in shaping secure and trustworthy relationships, emphasizing the importance of customer due diligence.
SignDesk presents a series of integrated APIs for background verification that can empower organizations with a reliable and efficient tool to ensure that the individuals they deal with meet their requirements, have trustworthy backgrounds, and align with the company’s values and standards. This workflow automation solution streamlines the verification process, making it more efficient and accurate.
By embracing the principles and practices of comprehensive background verification, individuals and organizations can forge connections built on credibility, thereby elevating the level of trust that underpins interactions in the modern world.