
As businesses rely increasingly on digital payment systems and financial processes, the possibility of payment fraud looms large. Fraudsters continuously develop new ways to exploit vulnerabilities, take advantage of naive organizations and commit payment scams.
To combat this growing threat, businesses must adopt advanced payment security measures. eNACH payment authentication is one such robust approach that provides a secure and reliable method for verifying the authenticity of payment transactions and minimizing the risk of fraudulent activities. By implementing eNACH into their recurring payment systems, businesses can prove that payments are authorized and authenticated electronically, minimizing the likelihood of unauthorized access or manipulation.
Payment Fraud on the Rise: A Threat to Business Security & Integrity
Payment fraud has become a widespread concern in today’s digital landscape, affecting businesses of all sizes. Perpetrators use a variety of tactics, ranging from expert cybercriminals to organized fraud networks, to accomplish payment theft.
According to the 2023 AFP Payments Fraud and Control Survey Report, since 2021, the number of fraud cases utilizing digital payment systems has increased by 10%. Among the many methods, commercial card fraud, business email compromise scams, checks, and wire transfers were found to be among the highly susceptible techniques used to execute payment fraud.
The same survey also showed that in 2022, more than one-fourth of firms (27%) could successfully recover at least 75% of funds lost due to payment fraud. However, nearly half of those companies surveyed (44%) could not recover any stolen money. It was also reported that over half of businesses with less than $1 billion in yearly revenue could not recoup money lost due to such payment fraud attacks.
Fraud Targets: Payment Methods Most Vulnerable to Fraud
With the takeover of digitization across the globe, many businesses are shifting their payments toward the digital landscape. While this makes way for improved & efficient transactions, it also opens doors for new types of financial fraud.
Criminals have numerous entryways along the entire payment chain, which they use as points of attack to commit payment fraud.
- Credit Card Payments
Fraud occurs when unauthorized individuals access commercial/corporate credit card information. The fraudster uses the company’s card information to perform purchases or transactions. Skimming devices and data breaches are the standard means criminals execute this kind of payment fraud.
Fraudsters use the data obtained by this method & exploit the card’s available credit limit to make online & offline unauthorized purchases, create false invoices, make cash advances at financial institutions, and carry out phishing attacks on the company’s employees and customers.
Criminals may also use the same techniques to manipulate virtual cards & prepaid cards.
- Checks
Checks are still one of the most susceptible payment fraud methods, and many firms encounter fraud activity via reviews because of their physical form and higher vulnerability to tampering. They contribute to payment fraud due to physical vulnerabilities and the simplicity with which they can be manipulated, duplicated, or counterfeited.
Fraudsters employ methods like stealing or intercepting checks during transit, creating counterfeit checks, forging signatures or altering information present on checks, check washing, and exploiting loopholes in the handling, storing, and disposing of cheques for illicit purposes.
- Wire Transfers
APP or Authorized Push Payment scam is a form of financial fraud in which individuals or organizations are deceived into authorizing a payment to a fraudulent account. This is a sophisticated type of financial fraud that uses wire transfers.
Fraudsters pose as legitimate individuals or firms, duping victims into transferring funds to bogus accounts. They take advantage of flaws in the company’s communication channels or employ social engineering techniques to trick individuals into thinking they are making genuine transactions and commit push payment fraud.
- Account Takeover
Fraudsters illegally acquire access to a company’s payment system or financial accounts & initiate fraudulent transactions. After they take over the account, the criminals make illicit purchases, transfer funds into their accounts, manipulate the account information, add more users, and alter transaction records to facilitate fraudulent activity.
Criminals gain access to a business’s financial account by taking advantage of security weaknesses, vulnerable passwords, compromised credentials, etc.
- Business Email Compromise
Cybercriminals gain unauthorized access to company email credentials, impersonate individuals from the organization, and trick customers, employees, and business partners into making illegitimate payments or providing sensitive information.
They do so by deceiving them into believing that the emails they have received are authentic. Through these phony emails, they request payments or request to share sensitive financial information, which results in financial loss for the targeted company.
- Invoice Manipulation
In this payment fraud technique, criminals alter legitimate invoices to trick customers and organizations into transferring funds to their accounts. The fraudster accesses the business’s database, email account, or other relevant invoice data systems.
Fraudsters use hacking, phishing, and other social engineering techniques to carry out invoice manipulation fraud & redirect money into their accounts. They may also pose as legitimate vendors or fabricate false purchase orders and send payment requests, tricking companies into making payments to fraudulent accounts.
Businesses can use various techniques to avoid financial fraud, including robust security methods such as eNACH payment authentication, which can improve the safety of their payment processes.
Origins of Payment Fraud: Common Modes and Patterns
Payment fraud can occur in multiple ways, and each of these modes presents significant financial, compliance, and reputational risks to businesses. Fraudsters use various methods to commit business payment fraud and exploit vulnerabilities in financial systems. Fraudsters commonly employ the following techniques:
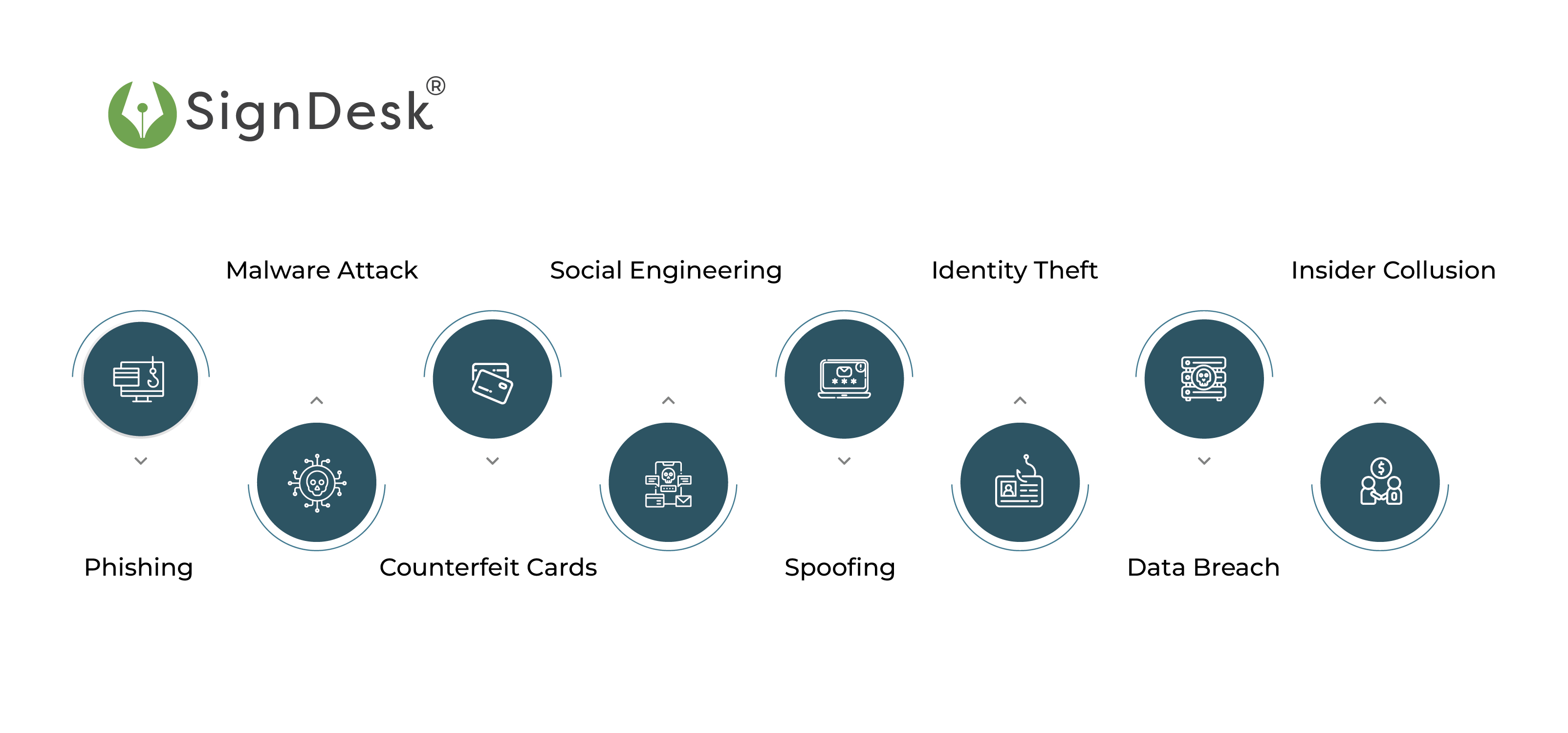
- Phishing: It is a type of cyber attack where fraudsters create deceptive emails, messages, or phone calls that appear authentic and dupe people into disclosing sensitive information such as financial details, account credentials, and other confidential data and engage them in fraudulent transactions. The most common way fraudsters phish individuals is through deceptive emails, texts, or websites from reliable sources like banks, online businesses, or reputable companies.
- Malware Attacks: Criminals use malicious software to infiltrate a company’s device, capture sensitive payment information like login credentials or card details, and initiate unauthorized transactions or redirect payment transactions to illegitimate recipients. They use this method to infect the company’s device with malicious software, gain access to sensitive financial data, and steal funds from their accounts.
- Counterfeit Cards: It is a technique in which fraudsters use a company’s stolen credit/debit card information to produce phony payment cards. These forgeries resemble genuine payment cards and can be used to conduct illicit transactions. Fraudsters access the cardholder’s financial information through various methods, including data breaches and card skimming.
- Social Engineering: It is a tactic fraudsters utilize to influence and deceive individuals into making unauthorized payments or disclosing sensitive payment information. Social engineering tactics exploit human vulnerabilities and use manipulative techniques to bypass standard security measures and target individuals directly, rendering them vulnerable to payment fraud schemes.
- Spoofing: In this method, fraudsters impersonate individuals or legitimate entities, like a reputed vendor or a bank, to get businesses to disclose sensitive information about their financial systems and manipulate them into making fraudulent payments. Criminals use spoofing to trick victims into providing financial information or making payments to unauthorized accounts by instilling a false sense of trust and legitimacy.
- Identity Theft: Criminals use the identity theft technique to exploit company systems’ vulnerabilities or target employees with phishing scams, social engineering, or malware attacks to obtain sensitive data. After receiving the financial data, they can impersonate the victim and carry out fraudulent activities like making illicit purchases, moving funds to fake accounts, or applying for credit or loans in the company’s name.
- Data Breaches: Fraudsters take advantage of security flaws in a company’s financial systems to get unauthorized access to sensitive data, which can then be exploited for fraudulent purposes. They infiltrate a company’s network and steal critical data, such as credit card numbers, banking details, and other confidential data, by exploiting vulnerabilities in security systems or employing sophisticated hacking techniques.
- Insider Collusion: Another mode of payment fraud occurs due to insider collusion, where trusted individuals within an organization team up with fraudsters to carry out unlawful transactions. Insiders may have access to sensitive payment information such as customer data, financial records, or authentication credentials, which they may exploit to enable illegal fund transfers. They may manipulate documents and tamper with financial transactions by misusing their access to internal processes and financial systems.
How Can Firms Recoup Funds After a Fraud Attack?
After experiencing payment fraud attacks, businesses can take these steps to retrieve funds and mitigate losses.
- Contact Banking Partners: Businesses must immediately alert their bank or payment processor after detecting payment fraud. The bank can launch an inquiry, freeze the affected account, and take additional actions to prevent further illegal transactions.
- Report to Authorities: Firms should notify the proper authorities, such as local law enforcement or the cybercrime cell, about the fraud incidence. They need to provide a detailed report of the fraud to help the authorities to launch investigation operations, track down culprits, and increase the possibilities of recovering the lost funds.
- Gather Evidence: Companies should gather all relevant documentation and evidence relating to the fraud incident. They can submit valuable evidence like transaction files, communication records, images, and other supporting data to recoup the lost money.
- Engage Legal Counsels: Depending on the degree and complexity of the scam, businesses can consider consulting with legal professionals specializing in fraud and financial crimes. They can provide guidance on legal options, assist in recovering funds through legal processes, and help manage any potential liabilities that may arise from the fraud.
- Work with Insurance Providers: If the company has fraud insurance, it should notify the provider promptly and start the claims process. Insurance plans may provide financial protection against specific types of payment fraud, assisting in recovering lost funds and covering any associated expenditures.
- Increase Security: Following a payment fraud attack, firms should assess and improve their safety measures to avoid facing similar attacks. Implementing multi-factor authentication, encryption technology, fraud detection systems, eNACH-based payment automation, and upgrading their financial security standards are some ways they can strengthen their security measures.
Ensuring Financial Security: Methods for Reporting & Reviewing Payment Fraud
With the increasing sophistication of fraudsters, businesses need effective mechanisms to identify, report, and review occurrences of financial fraud. This entails a combination of internal processes and engagement with external entities to report instances of offline/online payment fraud.
- Notify Law Enforcement Agencies: Reporting payment fraud and providing pertinent information and evidence to law enforcement agencies helps initiate an official investigation and involve the necessary authorities. Law enforcement organizations, like the police or CBI, can use their knowledge and resources to undertake comprehensive investigations and bring culprits to justice.
- File a Suspicious Activity Report (SAR): A Suspicious Activity Report (SAR) is a tool for reporting suspected financial transactions to regulatory authorities. Businesses can submit SARs to relevant regulatory organizations to report any unusual or suspicious payment fraud activities. SARs aid in identifying patterns and trends in fraudulent conduct, allowing regulatory bodies to take the appropriate steps to prevent additional fraud and preserve the financial system.
- Inform Internal Compliance Teams: These teams are responsible for investigating fraudulent activities, collecting evidence, and coordinating with relevant stakeholders to take appropriate action. By notifying compliance teams within the organization, businesses can ensure that the necessary protocols and procedures are followed to report and review payment fraud.
- Seek Assistance From Banking Partners: Banking partners play an essential role in assisting businesses in combating payment fraud. They have dedicated fraud departments that can aid in investigating questionable transactions, blocking accounts, and providing companies with beneficial insights and advice on fraud protection measures. Collaboration with banking partners improves the organization’s ability to detect, report, and recover from payment fraud occurrences.
Creating a Fraud-Proof Ecosystem- The Role of eNACH in Safeguarding Payments
eNACH, or Electronic National Automated Clearing House, is a robust solution essential in establishing a secure payment ecosystem and preventing fraud. By providing a safe and efficient means for recurring payments, eNACH plays a vital role in payment fraud prevention.
Businesses can use eNACH to automate debiting money from their customer’s bank accounts, ensuring that each payment is authorized and authenticated. This considerably decreases the danger of payment fraud by eliminating the need for manual intervention or paper-based instructions, which fraudsters can easily manipulate or access.
eNACH allows businesses to automate the debit process directly from customer’s bank accounts, thereby minimizing the fraud risk. The robust features of eMandate solutions, like stringent access controls, eNACH payment authentication, audit trails, and transaction visibility, help mitigate the chances of payment fraud to a large extent.
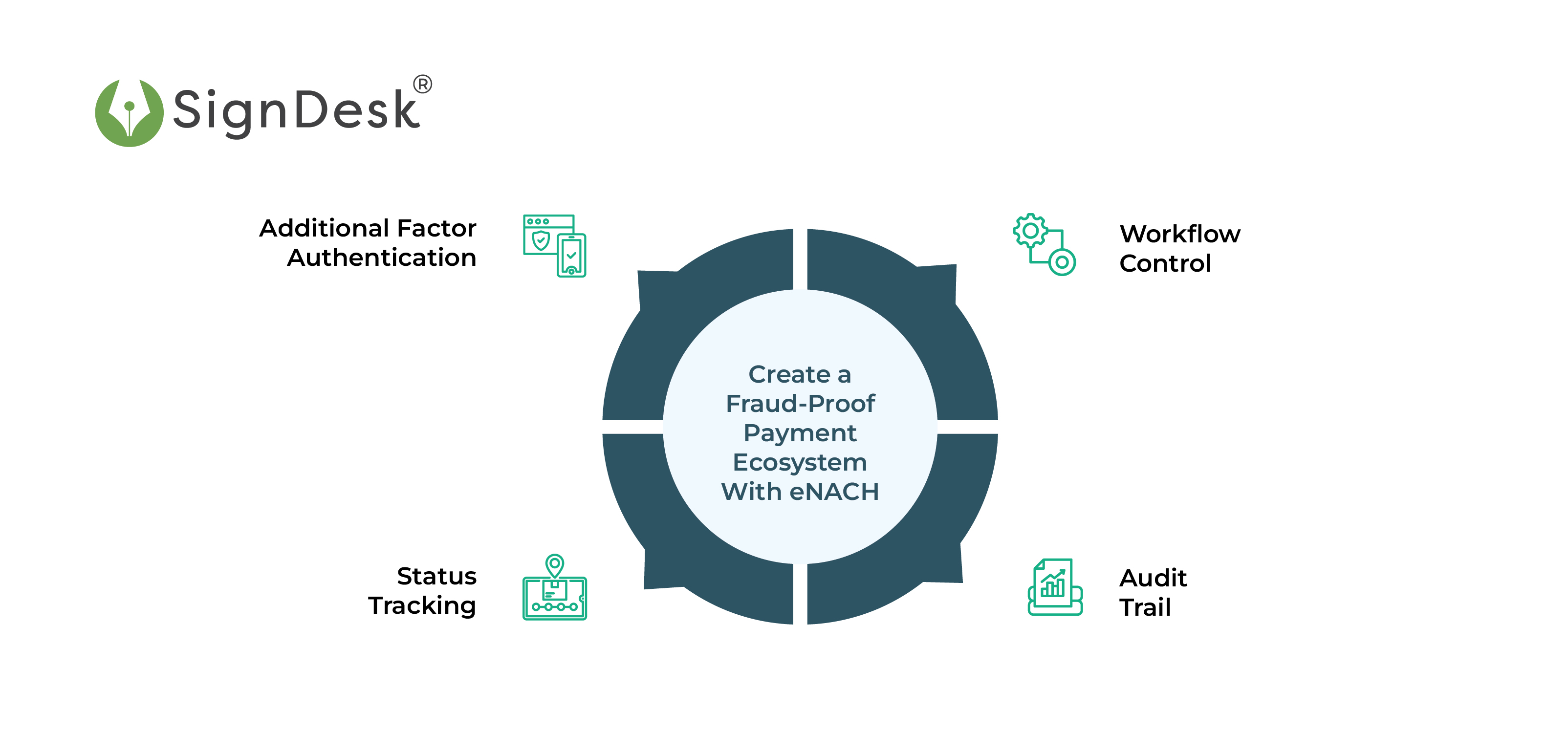
- Additional Factor Authentication (AFA)
AFA employs additional security mechanisms alongside regular login and password authentication for payments. It entails adding several verification aspects to validate user identities during login or other operations. These factors could be something the user knows (password), something they have (security token or mobile device), or something they are (biometric data such as fingerprints or facial recognition).
AFA adds extra protection, making it more challenging for unauthorized users to obtain access or carry out fraudulent transactions. This eNACH payment authentication technique aids in the protection of sensitive information and the prevention of unauthorized access to a company’s payment accounts and financial transactions, allowing them to receive payments from their customers securely.
- Status Tracking
The payment status tracking functionality of eNACH enables businesses to have real-time visibility of payment transactions and monitor them to detect potential fraud attempts early on. It allows them to actively monitor each payment stage throughout the payment cycle, from the customer’s eNACH payment authentication to identifying and resolving fraudulent activities.
With status tracking, companies can be aware of discrepancies like unauthorized modification of payment details, unexpected payment delays, etc. They can take the necessary precautions and mitigate any risk of payment fraud.
- Audit Trail
The eNACH audit trail provides a comprehensive record of all eMandate payment transactions and associated activities. It allows firms to monitor and examine transactional operations, detect abnormalities or suspicious actions, and investigate possible fraud cases. It captures and records transaction time and date, participant information, etc., to create a tamper-proof record of the full payment path.
The audit trail is a valuable analytical tool that allows businesses to monitor the flow of funds and detect potential vulnerabilities. This feature helps firms to implement appropriate payment fraud prevention measures and counteract the risk.
- Workflow Controls
Another significant feature of eNACH includes workflow controls that offer businesses robust control mechanisms and flexibility to tailor payment collection workflows per their requirements. These controls involve setting up debit limits, eNACH payment authentication, verification and payment status checks, validation protocols, and error-handling procedures.
Businesses can reduce the risk of fraudulent transactions by introducing workflow controls that guarantee payments comply with specified parameters. They offer additional security by flagging and prohibiting fraudulent transactions, prompting verification steps, and reducing the possibilities of payment fraud.
Secure Payments & Mitigate Fraud With SignDesk’s eNACH eMandate
eNACH, with its secure and efficient approach to recurring payments, plays a critical role in protecting businesses and customers from unauthorized transactions. eNACH ensures authorized and validated payments by automating the debit process straight from clients’ bank accounts, reducing the risk of fraud. It provides a transparent and secure payment mechanism that aids in the prevention of fraudulent activities and unauthorized transactions.
Businesses can use eNACH to prevent payment fraud and secure recurring debit transactions. Firms can automate and streamline payment procedures and maintain high security and compliance by utilizing SignDesk’s eNACH electronic mandate solution. Its robust online payment fraud prevention measures help companies identify potential risks and prevent fraudulent transactions.
Using eNACH allows organizations to develop a reliable and secure payment process with features like eNACH payment authentication that reduces the risk of payment fraud.
With eNACH eMandates, businesses can:
– Enable secure & regular payment collection
– Reduce manual handling of transactions
– Monitor transactions in real-time
– Set payment limits and controls
– Record virtual audit trails for compliance
Contact us to learn how our eMandate solution can streamline recurring payments and help prevent payment fraud.