An introduction to digital signatures
There is nothing more frightening than a forged or an invalid signature signed traditionally or electronically in a legal document, financial statements, contracts and other official documents.
In 2020, India recorded a 141% increase in ID frauds, resulting in Indian banks losing nearly Rs 1.85 trillion in 2020. Forged signatures are one of the primary methods of ID fraud & illustrate the lack of security prevalent in physical signatures.
This is why digital signatures are becoming the industry benchmark for signing documents & creating evidence. Digital signatures are the most secure way to authenticate the signer’s identity and are strong proof that the signer and no one else has signed the document in question.
Here’s an example of how a digital signature works and why it’s more secure than electronic and traditional signatures –
John needs to sign an insurance contract & his insurer sends him the contract to sign digitally. John clicks on a button to encrypt the contract using his private key, and this action creates his signature. He then sends it to the insurance seller, who’s already got a public key. This key decrypts the signature, thus validating it to ensure authenticity.
If the public key doesn’t or cannot decrypt the signature, it means that John didn’t sign the contract or that somebody altered the contract.
This stands in stark contrast to traditional wet signatures, which anyone can easily forge. Not so secure now, is it?
A digital signature is –
- Convenient to use
- Time-saving
- Useful in court to prove your participation in signing a document
- Legally valid and much more secure
- Efficient in signing bulk documents in a short time
All this sounds pretty nice, but what exactly is a digital signature?

What is a Digital Signature?
In layman’s terms, a digital signature is a code attached to a message or a document. Verifying the code proves that the message was unchanged or it was not tampered with. One should not confuse it with a digital signature certificate, which is equivalent to paper certificates that validate the holder’s identity.
Digital signatures have been developed as an application of cryptography and also find extensive utility in network security.
Digital signatures are easy to use & essentially involve the convenient click of a button. However, behind this simple process of clicking and selecting a signature source, is a complex workflow involving multiple instances of encryption and decryption.
Understanding how digital signatures work is integral to understanding why it’s secure.
How are digital signatures created?
A digital signature is created using hash algorithms or a scheme of algorithms like DSA and RSA that use public key and private key encryptions. The sender uses the private key to sign the message digest (not the data), and when they do, it forms a digital thumbprint to send the data.
It’s important to note here that all the tools used to digitally sign a document are numerical in nature. Digital signature solutions use crypto-algorithms to convert both the document to be signed and the private key (which is already in character form), into a new set of encrypted characters.
When a signed document is authenticated using the public key, the signer is aware of who created it & whether the document has been altered since being digitally signed. The decryption process gets back the original hashed document, and this can be compared to the encrypted hash, to determine the authenticity of the document & the digital signature.
To verify the identity of the signer and the digital signature, DSC or Digital Signature Certificate is issued. DSC is a secure digital public key that does all the decrypting & authenticates the identity of the holder. To understand what DSC is and why you require it, we’ll delve into the details further in this article.
The underlying process here is far from simple, and it takes multiple algorithms carefully designed to encrypt, decrypt, and authenticate messages & data to create a digital signature.
Here are a few of the most popular algorithms used for digital signatures.
Digital Signature Algorithm (DSA) and RSA
One of the algorithms used to create digital signatures is the Digital Signature Algorithm or DSA, the industry-standard cryptosystem used to create a digital signature.
DSA works based on algebraic properties of discrete logarithmic functions and modular exponentiations to create a digital signature that consists of two 160-bit numbers derived from the message digests and private key.
The other type of algorithm is RSA, named after its inventors – Ronald Rivest, Adi Shamir & Leonard Adleman, who first described it in the late 1970s. RSA is an asymmetric cryptographic algorithm used to encrypt and decrypt messages. Since it uses a public key framework, anyone can have the keys involved in decryption.
In Digital Signature Algorithms, a set of numbers is created, allowing the receiver to authenticate the origin of the message or document. In most cases, the digital signature used in data transmission will be private at the start.
Only the person performing the transmission can sign the document, but in the end, anyone can authenticate the signature.
A digital signature is created by pairing the public & private cryptographic keys. DSA by itself, however, can only be used to create a signature and not to encrypt data.
Hashing is another element in creating a digital signature. Hashing is a process of transforming data into a fixed-size output using a hash algorithm called a hash function. The output of the hash function is called a message digest or hash value.
Hash Function
A hash is a string of letters and numbers and numbers with a fixed length, usually with 256 characters. A private key encrypts the hash. The encrypted hash combined with the hashing algorithm is the digital signature. Hash functions go just one-way, unlike DSA and RSA, which are two-way encryption and decryption protocols.
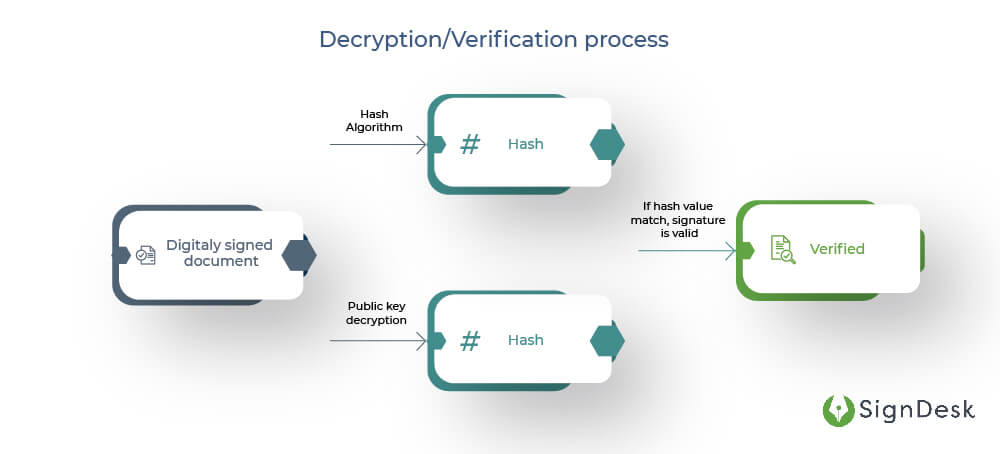
The hash value is unique to the hashed data, and even a slight change in data will result in a different hash value. This establishes the uniqueness of the digital signature & enables the signer to validate the integrity of the data when a person uses a signer’s public key to decrypt the data.
Suppose the decrypted hash does not match with the second computed hash of the same data, then it means that the data was tampered with or the private key did not correspond with the public key. If this happens, it means something’s gone wrong.
However, if the hash values match, then it can be concluded that the data and the signature are valid and verified.
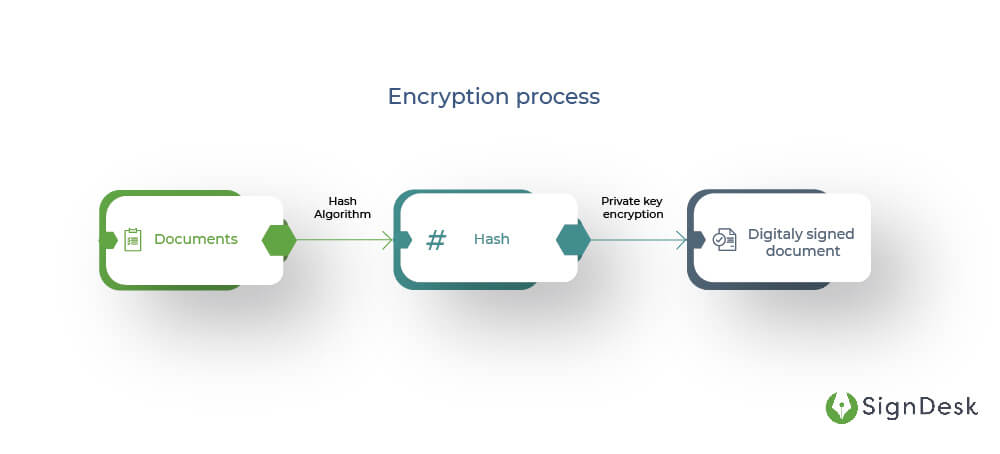
To sum it up, here’s how the digital signature process goes –
- To create a digital signature, DSA is used
- Keys generated using algorithms are used to sign a document
- The signature is created using your private key when you sign a document digitally
- A hash is created from the document, using a hash function
- Your private key encrypts the hash
- This DSA-encrypted hash is the digitally signed document
- The signed document is then transmitted
- The public key is used to decrypt the hash with the same hash function
- The signature is verified if the hash values match.
Whether encrypted or not, digital signatures can be used for any kind of message. If the document changes after you sign it, then the digital signature becomes invalid.
The security aspect of digital signatures isn’t limited to individual algorithms such as DSA & RSA, and is further bolstered by employing secure protocols & infrastructure.
PKI & PGP are necessary for digital signatures
The need for strong & unique signatures has resulted in the development of several cryptographic schemes & protocols designed to boost security. Public Key Infrastructure (PKI) & Pretty Good Privacy (PGP) are two examples.
PKI is a framework that generates, distributes, and validates public key certificates. DSA & RSA both run on PKI, since both involve the distribution of public keys. PKI’s current popularity in the crypto world is due to the fact that in PKI, the person who owns the document that needs multiple parties’ signatures, can send it to the parties, get their signatures on the document and then validate all their signatures using just one public key.
PGP is an encryption program and a type of PKI that uses symmetric key and public-key cryptography. In digital signature solutions that incorporate PGP, the public & private keys are also encrypted, providing an added layer of security.
Some security issues can surface when public keys are transmitted. Consequently, both PKI and PGP mitigate the issues that arise during document transmission and confirm that the sender owns the public keys. The sender’s identity is also verified this way.
Since no one can revoke the keys used to digitally sign if they’re compromised, both PKI or PGP play a huge role in digital signature security as they are instrumental in preventing impersonation. This reduces the possibility of signature keys falling into the wrong hands.
In conclusion, digital signatures are a great tool to have if you want to sign documents remotely, securely & instantly.
Now you know how digital signatures are created and how they work. Not everyone can easily use a digital signature. To be able to use it, an organisation needs to be authorised to issue it. This is where the CA (Certifying Authority) and digital certificates come into play.
Digital certificates and classes
A Digital Signature Certificate (DSC) is a secure digital (public) key that authenticates the identity of the holder. It uses PKI for data that has been encrypted by a private key.
The procedure for distributing DSC varies from country to country. In India, only the Controller of Certifying Authorities (CCA) can issue certificates to Certifying Authorities (CA). Following this, only a registered CA can then issue Digital Signature Certificates (DSC) to customers desirous of using digital signatures.
With the DSC, anyone can verify the authenticity of a digital signature on a document.
Now, why is DSC required?
DSC is essential for organisations or any individuals who sign documents digitally. Under the Information Technology Act 2000, the provisions to use digital signatures electronically are given to establish the authenticity and security of the documents made digitally. One can use digital signatures only when a registered CA issues a DSC for that specific digital signature.
There are different classes of digital signatures certificates based on the information required to verify digital signatures and the generation mechanism of the private key stored in CAs.
Classes of DSC
Class I – Class I of DSC is issued to individuals and requires aadhaar eKYC biometric or paper-based application forms or video verification.
Class II – In the case of Class II, the identity of a person is verified against a trusted pre-verified database and the private key generation is stored in a cryptographic hardware device validated to FIPS 140-2 level 2.
Class III – This class of DSC is just an upgraded version of class II and can be used to participate in online auctions, e-tendering and online bids. Class III is the highest level of DSC.
How do I create a digital signature online?
SignDesk provides award-winning & automated digital signature services. We’re a CCA-certified CA for digital signatures & offer an eSign workflow solution; with features to add multiple signers, create documents online using templates & track your documents as they’re sent out to be signed.
To create a digital signature using SignDesk, all you have to do is log in first and upload a document. Then, invite signers to sign the document & optionally impose a signing order. Your signers will receive the document and eSign it online, all within minutes.
We also provide options for Aadhar eSign, electronic signature, PAN-based signature, and DSC signature. Aadhar eSign is the safest and secure type of digital signatures and is the most opted-for option.
Sign up for free now to sign documents online with unlimited electronic signatures.